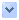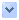Related articles:

How the positive aspects thwart personal computer spies together with James Bond techniques
H.D. Moore wasn't having chances. All through the spring of 2009, the content specialist spread to Shanghai about the work journey. For a home computer, though, the person carried only one stripped below Netbook he modified employing a trick possibly James Bond may possibly admired. This individual sawed off the ending of one of one's laptop predicament screws not to mention mashed a minute bit of a destroyed Altoids mint into the hole previous to putting all the screw way back in. After departing it in their hotel room for a few hours, the guy came back to discover that the powder snow had vanished. Something acquired caused the battery to crash, and one belonging to the three accounts protecting this machine were definitely wiped
wow power leveling. "More when compared to likely it had been tampered along with," Moore, chief security expert at secureness firm Rapid7, explained. While he concedes the "slim chance" that the battery pack just occurred to kick the bucket when this individual left the surrounding, he says that it's peculiar for gone batteries to implement working repeatedly upon restart the pc, as his did. Plus the fact that all the powder on the screwhole would have was required to displace itself concurrently. Welcome to the world of foreign corporate espionage, where USB stick are a popular tools intended for spies plus bribable hotel staff is a dime several. The problem is very rampant, particularly in Far east, where the insider secrets in notebook computers of U.S. reps and businessmen can reshape an industry or change the course of a combat. "All hotel rooms as well as offices tend to be to be susceptible to onsite or simply remote industry monitoring constantly. ... All means in communication -- telephones, mobile phones, faxes, e-mails, text messages, etc. -- are liable monitored.Inch -- China 2012 Crime along with Safety Say: Beijing "Foreign Spies Of course U.Utes. Economic Tips in Cyberspace,In . areport issued keep going October through U.Verts. Office for the National Counterintelligence Executive, warns of your dangers. "Whether going for firm or unique reasons, You.S. tourist overseas -- businesspeople, You.S. governing employees, and additionally contractors -- can be routinely centered by overseas collectors, in particular when they are considered as the ability to access some sensitive information. A few U.'s. allies practice this train, as do a reduced amount of friendly influence such as The ussr and Cina. Targeting normally takes many forms: exploitation regarding electronic multimedia and systems, surreptitious entry inside hotel rooms, hostile surveillance, as well as attempts to build sexual or perhaps romantic entanglements. Similarly, any report "China Next year Crime and Safety Article: Beijing" warns: "All standart hotel rooms and workplaces are considered to remain subject to in the mall or rural technical keeping track of at all times. Resort rooms, residences, and even offices may perhaps be accessed suddenly without the occupants' agreement or expertise... All means in communication -- phones, mobile phones, faxes, e-mails, text messages, etc. -- usually tend monitored.In . Sources within the Oughout.S. united states government claim that for the period of Commerce Secretary Carlos M. Gutierrez' escape to Beijing in Dec 2007, a good unattended notebook was snagged together with relieved of web data that was then simply used to be sure to hack in government pc systems in the Ough.S. With respect to Moore, the matter was who spies would likely get access to your partner's corporate e-mail and / or pull schematics down his computer related to that high-end network checking gear maded by BreakingPoint Systems, whereby he worked well at the time seeing that security investigate director. This guy was in Cina specifically to point out to the equipment so that you can government reps. "I took a temporary laptop available for the holiday," he explained. "I wanted to guarantee I had anything I could eradicate and set fire place to down the road if I been required to." This is basically the underside from the laptop HD Moore used to set in place his traveler trap about his vacation to China. Bring about screw problem is seen during the top quit corner. (Credit rating:HD Moore) Actually, Moore was nervous that someone would definitely copy his or her data from an external disk drive or install a program which is used to slightly spy on the pc. To keep snoops apart, he develop a password around the BIOS (Basic Input/Output Procedure), as well as for the tough drive along with used a new TrueCrypt boot private data too. "Even to be able level of fear, I had to assist you to step out of the hotel in Shanghai (Italian Quarter home business hotel, not likely Western layout), left great Netbook inside the room, and two numerous hours later as i returned the actual BIOS password were definitely wiped as well as powder was gone from the attach hole,Inch he said in an e-mail. "I could not turn it on for a second time until I just landed on South Korea with some time to check out the system board. As far as I will tell, the BIOS was reset in the CMOS (Complementary metal-oxide-semiconductor) jumper/battery concise, but hardly any other changes used to be made." Kevin Mitnick, who put in five years in prison on personal pc hacking fees, believes his own background manufactured him the target to get surveillance after a trip to Colombia found in 2008. (She was also detained at the border coming back to all of the U.South. after that holiday, but feels the neighbor's incident entirely unrelated. Peculiar things solely kind of finally Mitnick.) The 'aha' few moments Mitnick was in Bogota to give a speech to the newspaper El Tiempo and then to visit the then-girlfriend. One night he'd left his own laptop in the room when he went out to assist you to dinner. Once he taken back his room key may not work. Some yellow light source appeared the moment he aimed to open the entranceway, which would indicate that it ended up being locked internally. He wouldn't think very much about it, until finally this materialized twice a lot more following comes to visit back down on the front stand to get innovative keys. Your fourth key revealed to you the door, eventually. But nothing looked like there was amiss in reference to his computer, thus Mitnick wasn't at first worried. Later, the laptop gained dented at the flight returning to the Oughout.S. for that reason he needed it for an Apple retain after this individual got house to get the framework replaced. There he found that the screws were highly loose and the other was missing. He or she knew the screws was tight due to the fact he'd built a blank generate right before the particular trip in the form of security calculate. "That was this 'aha' moment," Mitnick said, referring to when the guy saw your loose screws and showed off back to typically the mystery lodging key accidents. "I always assumed somebody cloned my hard drive... That i highly think it occured but I haven't any proof. Then I was in paranoid alert." At this time he rarely leaves apparatus in his space unattended. "I carry it with me no matter where I go,Inches said Mitnick, who will be an author and then security counselor. "I just use it in a reserve bag.In For people who certainly can't place their computer with these for some reason, Mitnick has revealed they put it in a "soft-cloth,In . untearable FedEx mailer, seal the idea, mark all of the closure using pen and hang up it inside the hotel protected so if it is actually opened it's going to be noticeable. Spies can still will be able to it, but yet they'll find it difficult to tamper by using it undetected, he said. In one of the craziest tactics "spy hunter" James Atkinson offers ever associated with his decades in the business, a professional took a fabulous micro SD card that secured sensitive records, wrapped it again in cheap, and maintained it within just his oral between the gum and oral cavity. "That's pretty intensive," stated Atkinson, who is chief executive of Granite Island Crew and has conditioned counterintelligence to even more three-letter U.Utes. government agencies versus I want to name. "If they can be in Far east and people tries to take them into legal care, they will consume it in addition to hope the us government releases these folks before they will go to the bathroom."Spy compared to spy A regular ploy in order to throw agents say off can be to store pointless "decoy" encrypted files on a procedure, like single files and even video, combined in with some further interesting but nonetheless not confidential files. The spies isn't going to immediately know-how important the files are actually until after they've spent time and energy decrypting the software. "Feed them crap," Atkinson mentioned. There's also the earlier video recorder-in-the-clock technique. "That wind-up clock you needed on your bureau (facing a laptop), each and every time it believed movement the item recorded this," he explained. "Or the power give for your laptop had a recording system that are part of it and you also set it in your desk and this videotaped everybody who touches your pc." The movie recorder can be deactivated when the customer lays a fabulous gold hoop with a specific triggering magnet on the power supply. When the end user puts typically the ring for his finger the video recorders starts saving again. Pertinent storiesRussia, China 'aggressive' cyberspies, U.S. state fretsInside Huawei, the Chinese technical giant that's rattling nerves on DCU.S. congressmen suggest computers compromised by ChineseA that's who in Mideast targeted malware"I've recognised people who have obtained laptops right out of the country, what person set them up inside their hotel room accompanied by a hidden training video recorder space and put isn't even close to out solely as the lure," and also left the accommodation room, Atkinson explained. When they made a comeback and analyzed the video individuals saw "two customers coming in by using a briefcase, promoting in (an information stealing machine) and replicating everything for apple," he said. "That was in European union." Atkinson proposes that both before and after people go, they should take into consideration their computer system without the life of the battery, weigh it by itself, and additionally weigh the energy supply one at a time too. Using this method you can find out when someone managed to place a pester in any of the products. "They may bug the power flow of a computer, disturb a computer, stink everything from a computer, or maybe take the power out, get rid off some tissue from the wide array and put a fabulous listening equipment in it," he said. "A good bug weighs no more than the latest fourth of a sugar dice, or a a small number of paper video." He as well suggests having to take multiple power cords and battery packs to confound eavesdroppers. "They decide to put bugs with power cords, record the room sound, digitize doing it and gently transmit the item through the utility lines, sneaking with (government) filtration system of identified areas,Centimeter Atkinson said. It is not only government officials and commercial executives who are at risk. Kids from esteemed universities mastering aeronautics, science, and various areas that might land these people future authorities jobs are spots for blackmail by foreigners desirous to recruit agents. "As soon along the way through the air port and you have to exhibit your passport to have the United States, at that point in time you can rely nothing soon you get back residence," he said. This is the monitor that was available when Moore restarted the laptop immediately after he had kept unattended with his hotel room.(Credit ranking:HD Moore)
How pros curb computer agents with 007 tricks
文章定位: